Editor’s Brief
Last week, was about Mach Industries building drones.
This week, is about stopping them
Enter DroneSec—a threat intelligence platform tracking unmanned systems before they strike.
Reply directly to this email with feedback or interesting companies.
September Partnership Slots Now Open
Defense Tech Signals features one partner per issue—always editorial, always aligned.
September is now open.
If you’re building something serious for the national security ecosystem and want to get in front of founders, investors, and decision-makers—this is the channel.
→ View the Partnership Page
→ It’s Not For Everyone, But Perfect for a few.
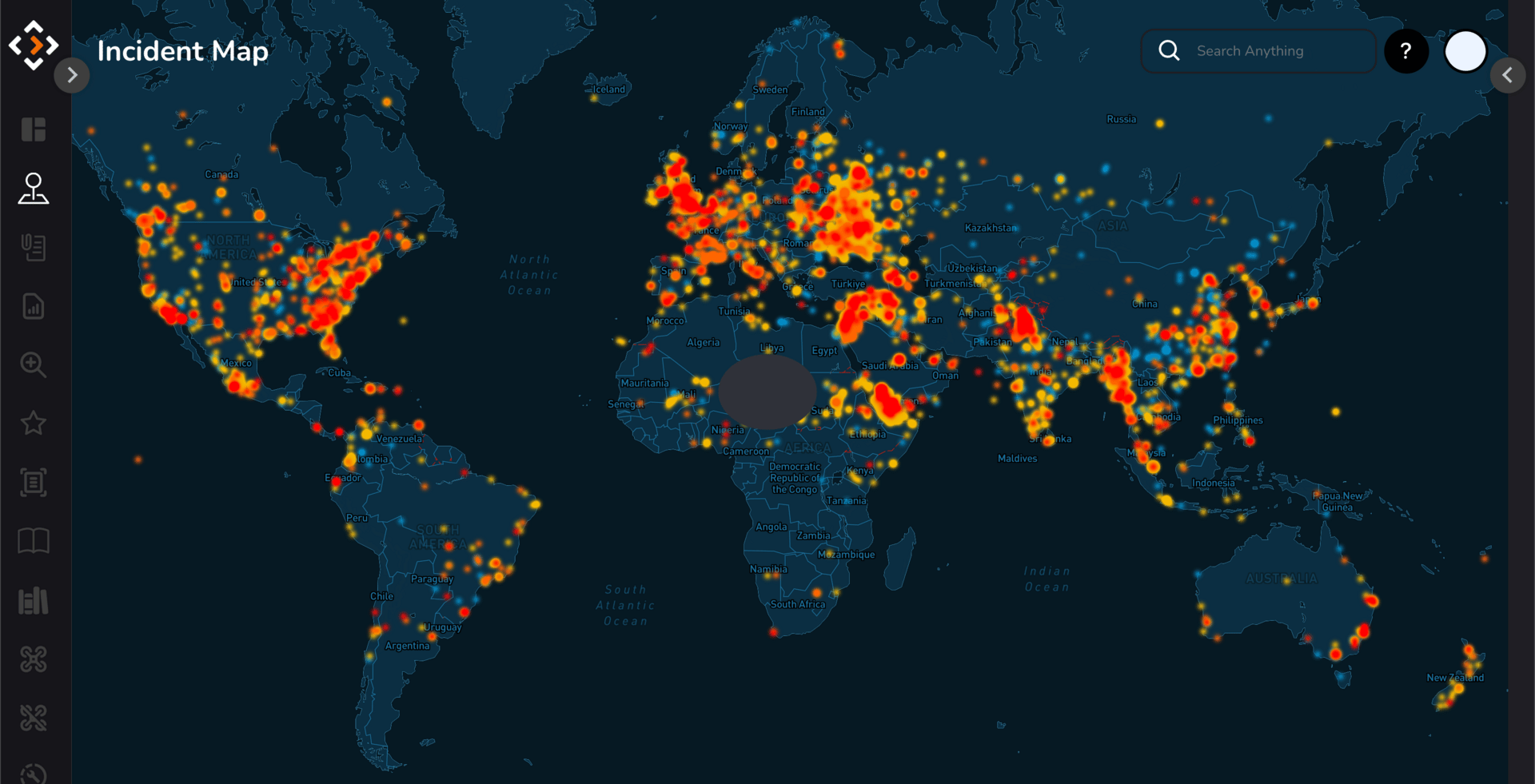
DroneSec Incident Map
Signal Brief: DroneSec - The Intel Behind Drone Warfare
DroneSec is a software-first threat intelligence company that aggregates, analyzes, and disseminates unclassified global drone incident data through its UxS Threat Intelligence Platform. The system draws from more than 1000 sources daily, including surface, deep, and dark web monitoring.
It has quickly become the default drone threat database by clients across all branches of the U.S. Military, special forces and federal agencies, along with international customers in the Five Eyes (FVEY) and NATO communities.
Origins & Vision
Founded in 2016 by Mike Monnik, a red team operator with experience at the Australian DoD and BAE Systems Applied Intelligence, DroneSec began as a side project to track emerging drone threats, countermeasures, and operator tactics.
Monnik’s experience hacking drones for cyber security to infiltrate high security facilities led to the realization that the Ukrainian FPVs, Mexican narco-drones, and hobbyist kamikaze platforms were variations of the same problem.
DroneSec formally launched its platform in 2020. By 2022, it expanded coverage across air, land, maritime, and space domains and in 2023, it secured several six-figure contracts with tier-1 customers directly interfaced into the C-UxS problem set.
Also in 2022, it quietly published the OPSEC Guide for Drones, used by Ukrainian forces and built from years of observing tactics, countermeasures, and security lapses around the globe. While most C-UAS firms focus on hardware and jamming, DroneSec maps global adversary patterns and behaviors to inform better defense planning.
Key Takeaways
Proactive Intelligence Advantage — The platform delivers early threat insights up to eight months before conventional intel cycles.
Trusted by Institutions — DroneSec has taken part in INTERPOL, NATO and United Nations events.
Complement to Kinetic Systems — Augments intel and C-UAS teams with threat profiles, TTPs, and adversary intent data.
Across all Domains — Tracks adversary innovation across all autonomous systems including Ground, Maritime, Air and Space.
Tech Radar:
DroneSec’s flagship offering automates the aggregation, categorization, and dissemination of drone threat data. It's used for red team wargames, adversary platform recreation, tabletop exercises, and intelligence ops.
Key Capabilities
Real-time Intelligence: Daily, weekly, and monthly drone threat coverage
Automated OSINT Collection: Reduces analyst workload with structured, searchable databases and source tagging.
Threat Actor Analysis: Detailed information the tactics, techniques, and procedures (TTPs), make and models of drones and counter-measures used by different groups
Technical Component Analysis: End-to-end supply chain analysis of the components used in UAS and the effects they might have on operations
Counter-UAS Intelligence: Information on C-UAS systems effectiveness and performance in the field, including counter-counter measures, non-standard control frequencies and RF signatures

Example Incident Brief
C-UAS RFI Sharing Portal — A central database where the intelligence community (IC) requests and share information reports with each other on advanced UAS/C-UAS topics
Intelligence-based Threat Briefings — Monthly threat briefs covering emerging and novel techniques in drone contraband, counter-measures, attack planning and tech
Technical and Adversary Intelligence — Technical documentation and manuals sourced from covert collection and regional contacts.
The company also launched a Stolen Drone Information (SDI) database, akin to license plate recognition for drones, using DroneID metadata.
Check out a full demo of the platform on The Drone Ultimatum podcast.
Market Signals
Funding & Growth
Disclosed Capital: Bootstrapped
Revenue Model: SaaS subscriptions
Employees: < 20
Contracts & Government Traction
FBI — $750k Firm Fixed Price contract.
U.S. Army C5ISR Center — Subcontracted via CACI on a $414M IDIQ for software/firmware support
Air Force Material Command — Specialized drone threat intelligence via Amentum
DLA Troop Support — UAS adversary threat intelligence via NOBLE
Tired of compliance drama?
That enterprise deal? They just asked for SOC 2. Traditional path: 6 months, $100K.
With Delve: 15 hours. Our AI handles the busywork, and our experts help you close faster.
Lovable did it in 20 hours.
11x unlocked $2.3M.
Book a demo—code BEEHIV1K gets you $1,000 off.
Looking Ahead
The West once dominated intelligence through secrecy. For decades, the CIA and West German intel quietly owned Crypto AG, a Swiss encryption firm, reading the communications of 120+ countries
Today, intelligence is online.
Every iPhone is an ISR node. Hobbyists track hypersonic tests using commercial satellites. And while China is hacking us, more often, they’re just watching us “build in public.”
Vulnerabilities aren’t always technical. Sometimes their just human.
Engineers want to look smart. Startups want attention and funding. Soldiers document everything. That instinct to share has become a goldmine for modern intelligence gathering.
But it also offers an edge: if we can out-process our adversaries, the same data that exposes us can empower us.
Yet too much of the West’s drone doctrine is still shaped only by Ukraine. The next fight might look more like Douliu and less like Donbas.
Monnik calls these Environment-based threats.
In Haiti, DJI drones are used for street warfare. Myanmar’s insurgents retrofit crop dusters into rocket launchers. Across the India-Pakistan border, drone activity plays out under deep political and airspace constraints.
And near Taiwan, China is testing swarms of autonomous systems that will demand entirely new playbooks.
Each region brings its own geography, ideology, and toolkit—and spawns new tactics in response. That’s why we need real-time, environment-specific intelligence built outside the traditional pipeline.
The companies and commands preparing for the next conflict need this data now, not in next year’s Big Beautiful Bill.
DroneSec is one of the first to build that layer. A global, multi-domain map of unmanned system behavior with the speed, granularity, and relevance today’s conflict zones demand.
China and Russia will build their own versions.
But right now, our advantage is time.
Let’s not waste it.
Challenges
Intentional Propaganda: Adversaries stage or recycle footage to mislead intelligence efforts (e.g. Myanmar drone strike videos reused in the Thailand–Cambodia conflict).
Synthetic Media: AI-generated or edited visuals create false narratives, such as fake images of fiber-optic drone cables.
Connectivity Gaps: OSINT relies on both upload and access. In low-bandwidth or censored regions, critical data can be delayed or lost entirely.
Bottom Line:
The U.S. still leads in intelligence—but stovepiped, decade-long cycles can’t keep up with drone threats evolving weekly.
China understands this.
They seed the internet with teaser tech (robo-dogs, maple-leaf drones, mosquito UAVs) then watch as Western experts publicly debate capabilities, weaknesses, and countermeasures.
That discourse becomes free R&D for PLA war-gaming.
Companies building for Ukraine’s FPV fight may win today.
But if the battlefield shifts to the Indo-Pacific, their tech risks irrelevance.
Staying ahead means tracking how threats and tactics evolve, not just who makes them.
And that’s the layer DroneSec is building.
Stay Ahead of Defense Innovation
Not just because it’s content
But because the future is being built. And you want a seat at the table.

